The European Commission (EC) organised another eMRTD interoperability test. This time the event took place in Ispra at the Joint Research Center of the European Union. The objective of this interoperability test was to assure that countries and companies have established a stable PACE protocol in their eMRTD, respective ePassports, and ID cards.
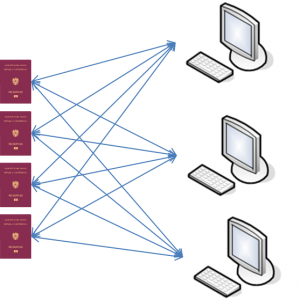
Test setup of eMRTD interoperability test
Every participant had the chance to submit up to two different sets of documents with different implementations. Altogether there were 42 different samples available at the beginning of the event. 2 samples didn’t pass the smoke test and one sample was not suitable to be tested by the labs. All remaining samples were tested in two different test procedures: crossover test and conformity test. Twelve document verification system providers with 16 different solutions took part in the crossover test. And 23 document providers threw 42 sets in the ring (28 countries, 14 industries).
In this blog post the conformity test is focused on, because protocols are in foreground in this kind of test. There were three test labs (Keolabs, UL and secunet) taking part in the interoperability test with their test tools to perform a subset of “ICAO TR RF Protocol and Application Test Standard for e-Passports, Part 3” (Version 2.10). The subset includes the following test suites and test cases:
- ISO7816_O: Security conditions for PACE protected eMRTDs
- ISO7816_P: Password Authenticated Connection Establishment (PACEv2)
- ISO7816_Q: Command READ and SELECT for file EF.CardAccess
- LDS_E: Matching between EF.DG14 and EF.CardAccess
- LDS_I: Structure of EF.CardAccess
- LDS_K: Structure of EF.CardSecurity
- LDS_D_06: Test case to perform Passive Authentication
Information concerning documents
The document providers describe in the implementation conformance statement (ICS) the features of their chips. Not all ICS were fulfilled consistently, so the following information concerning the documents should be read carefully. Concerning the LDS version 16 providers reported version 1.7 to be used in their documents. And three reported version 1.8, while all others don’t deliver any information concerning the version number.
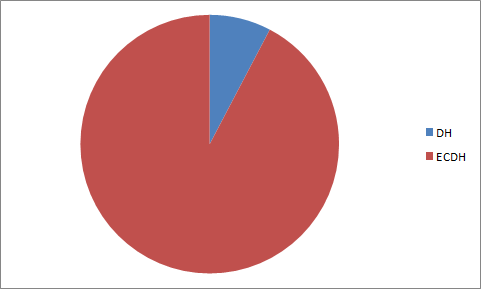
The following diagram describes the relation between DH and ECDH in PACE:
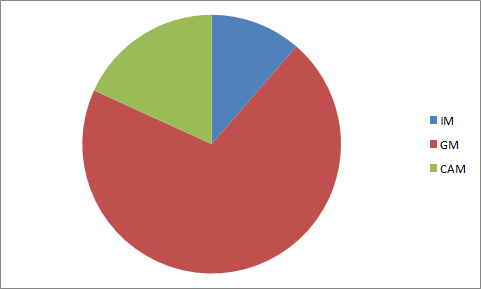
The following diagram describes the relation of the mapping protocols in PACE:
16 documents supported besides the MRZ also a CAN as a password to get access to the stored data.
Again, the number of PACEInfos store in EF.CardAccess varied:
- 28 documents stored one PACEInfo,
- Eight documents stored two PACEInfos,
- One stored each three, seven or ten PACEInfos.
Investigations concerning EF.ATR/INFO in documents
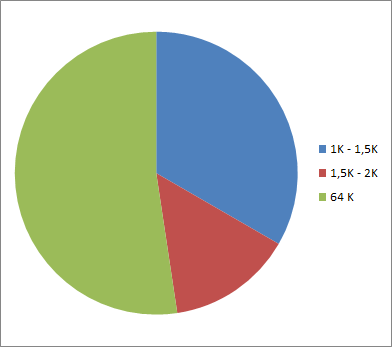
The file EF.ATR/INFO allows storing some information about the chip, that allows the reader to handle the chip optimally. On this way the chip can offer the ideal buffer size used with extended length during reading and writing. In context of the event I had a closer look at EF.ATR/INFO. 26 documents of 42 stored an EF.ATR/INFO but 5 of them don’t offer information concerning extended length and buffer sizes there. So at the end I’ve investigated the reading buffer sizes of 21 documents of the eMRTD interoperability test with the following result:
- Seven documents support buffer sizes between 1 and 1.5 KByte,
- Three documents support buffer sizes between 1.5 and 2 KByte,
- Eleven documents support buffer sizes of ~64 KByte.
With these large buffer sizes data groups like DG2 storing the facial image or DG3 storing the finger prints can be read in only one command. This allows the inspection system to read the content of the chip faster and improves the reading time at eGates.
Results of conformity testing
During the conformity test, all three test labs performed 18.135 test cases altogether. Less than 1 percent of these test cases failed during the conformity test.
Overall results (layer 6 and layer 7):
- Passed: 11.563
- Failed: 155 (0,86%)
- Not applicable: 6.417
Layer 6 (16.614 test cases performed):
- Passed: 10.885
- Failed: 124 (0,74%)
Layer 7 (1.521 test cases performed):
- Passed: 679
- Failed: 32 (2,10%)
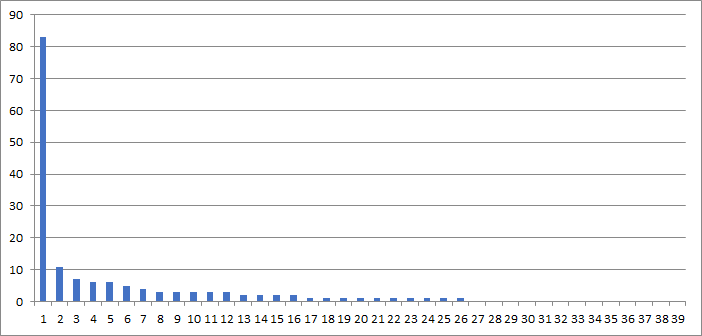
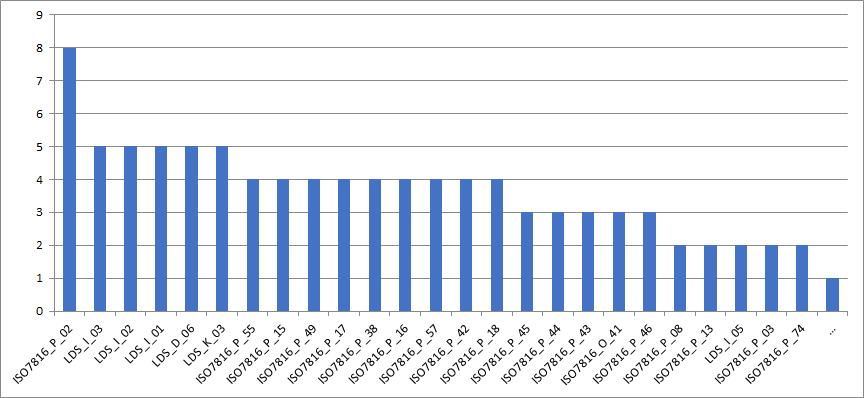
The following diagram shows failed test cases per document during the eMRTD interoperability test:
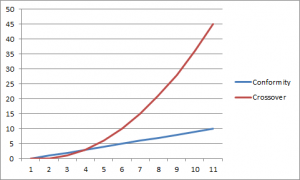
The diagram below shows the number of failure per test case during the eMRTD interoperability test:
Observations during conformity testing
- There are minor differences between implementation conformance statement (ICS) and chip.
- Test results differ between test labs in some test cases.
- There are differences in handling errors at the test tools and labs (e.g. no CAN causes a failure at the one lab and a ‘not applicable’ at the other lab).
- Relatively more failures on layer 7 (personalisation) than on layer 6 (COS).
- Very good quality of chip and personalisation.
- Improvements during the last interoperability tests in London 2016 and Madrid 2014.
- Stable specifications (BSI TR-03110, ICAO Doc 9303) and test specifications (BSI TR-03105, ICAO TR Part 3).