The GSM Association (GSMA) has released a new requirement specification focusing on Secured Applications for Mobile (SAM). In this specification the capability allowing cellular connected devices (e.g. smartphones) to use a wide range of secured applets within an eUICC (embedded universal integrated circuit card) is described. Applets specified here can be managed by a service provider and are cooperating with applications running in the device itself. The focus of the specification is on the eUICC where the secured applets will operate independently and outside of any eUICC profile.
The requirement specification with the title SAM.01 is published on the GSMA website in the following link: https://www.gsma.com/newsroom/resources/sam-01-secured-applications-for-mobile-requirements
Use case: mobile eID as a secured applications for mobile
The usage of mobile devices for mobile services is one of the dominant trends we can see worldwide. Mobile devices replace the personal computer at home or at office. For access to online services the mobile device is getting more and more important. New applications are often only offered for mobile devices (mobile first). Based on this trend the mobile device is becoming the most common interface between the customer and the service providers.
For the digitalization of business process, the secure identification and authentication of end customers is a key requirement. The eIDAS regulation No 910/2014 of the EU is defining three levels of assurance (LoA) for electronic identification. The two highest levels “high” and “substantial” are demanding the usage of secure elements (see BSI Technical Guideline TR-03159 Mobile Identities). To achieve these levels the usage of an secure hardware token is essential. One of these token could be an eUICC and the usage is specified in SAM.
This secure hardware token is a central element for several mobile identities that are currently under development, like ICAO Digital Travel Credentials (DTC), mobile Driving License (mDL) specified in ISO/IEC 18013-5 or in general building blocks for mobile ID (ISO/IEC 23220). Last but not least the German identity card (ePA) will be derived to a smartphone to use the online identification directly on the device.
You can find a description of current mobile ID projects and standardisation work in my article “Digital and mobile identities” which was published in the context of Open Identity Summit 2020.
As soon as the eUICC is a well-specified secure platform, it is the perfect platform for hosting mobile ID applications which are offering high security for the service provider and also for the end user.
Architecture of SAM
The following figure describes the architecture of Secured Applications for Mobile (SAM) as specified by GSMA:
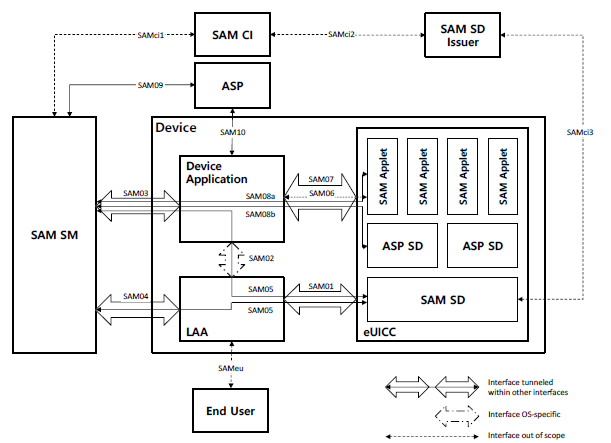
On the left side you can find the service manager (SAM SM), which acts on behalf of the Application Service Provider (ASP) and is in charge of managing SAM Applets through SAM Commands. On the device itself you can see the device application (e.g. provided in an app store by the ASP), the local applet assistant (LAA) and – of course – the eUICC. The eUICC offers a security domain (SAM SD, also known as common security domain (CSD)) including an ASP SD where the SAM applets are located. The SAM applet can be used to assure the security of the device application by storing keys or holder data, performing encryption, signing etc.
Next steps
The work has not finished with the release of the requirement specification. All the requirements must be incorporated into a technical specification where all details are described on the level of bits and bytes. To assure that current developments in other working groups are also involved (and to assure that the wheel is not reinvented a second time) GSMA is working with external organizations like GlobalPlatform or ETSI. On this way we will see several interoperable applets running on eUICC allowing high security in the near future.



