Introduction
A few days before the Eclipse Neon release, the Eclipse Foundation has released several projects in context of IoT (Internet of things). The Eclipse IoT working group is engaged in projects like SmartHome, Kura, Paho and OM2M.
 The Internet of Things is all about connecting devices (sensors and actuators) to the internet. You can find these devices in automobiles, wearables, industrial factories, homes, etc. A key challenge is the complexity of implementing an IoT solution where you need to deal with various hardware platforms, manage the IoT gateways to connect the devices to the internet, manage the connectivity and interoperability, and integrate the data in the existing systems and databases.
The Internet of Things is all about connecting devices (sensors and actuators) to the internet. You can find these devices in automobiles, wearables, industrial factories, homes, etc. A key challenge is the complexity of implementing an IoT solution where you need to deal with various hardware platforms, manage the IoT gateways to connect the devices to the internet, manage the connectivity and interoperability, and integrate the data in the existing systems and databases.
An important way to reduce this complexity is to create reusable libraries and frameworks. As a result these frameworks are abstract and implement key features. Consequently right here is the approach of Eclipse IoT delivering several technologies combined in an open source stack with all key features and standards that you need to develop your own IoT solution. Furthermore the Eclipse Foundation set up a community with more than 200 contributors to assure the enhancement of the IoT stack.
The current release includes Eclipse SmartHome Version 0.8 and Eclipse Paho Version 1.2. The projects Eclipse Kura and Eclipse OM2M will be available later this month. Additionally, the foundation starts a new project proposal called Eclipse Kapua. Goal is to create a modular integration platform for IoT devices and smart sensors. On this way there will be a bridge between Operation Technology and Information Technology.
Eclipse IoT
The Eclipse IoT ecosystem contains standards, gateways and of course frameworks. The following paragraphs will describe these modules. In addition you can find a reference to an Eclipse project that is relevant in this domain. Please keep in mind that this list is not complete, there are currently 24 different projects available in context of Eclipse IoT.
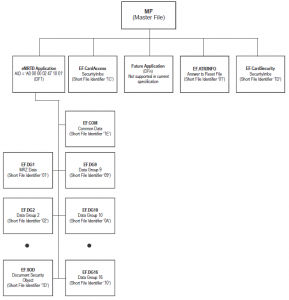
IoT stack
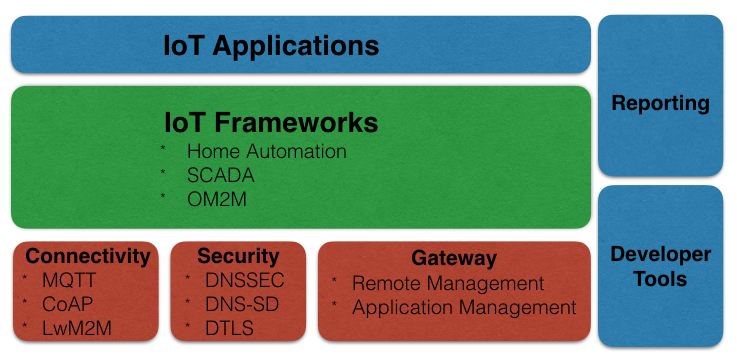
The following graphic describes the structure of Eclipse IoT stack. The stack includes frameworks, open communication standards and a gateway to assure management services. Consequently most modules based on Java and OSGi. OSGi describes a modular system and service platform for Java that implements a complete and dynamic component model. Finally the Eclipse IoT stack with its components addresses all key requirements in IoT: interoperability, security and connectivity.
Open communication standards
It’s an elementary feature in context of IoT to provide several mechanisms for protocols used in this domain. All devices must be connected, secured and managed. On this way the Eclipse projects in the IoT ecosystem supports the relevant protocols and standards:
- MQTT: Eclipse Paho delivers a MQTT client implementation (Java, C/C++, JavaScript). The corresponding MQTT broker is implemented in Eclipse Mosquito (implementation in C). MQTT (Message Queuing Telemetry Transport) is a light-weight publish and subscribe messaging protocol specified in ISO/IEC 20922. Almost the new version 1.2 of Paho includes for example WebSocket support for Java and Pythons clients.
- CoAP: Eclipse Californium delivers the CoAP standard in Java, including DTLS support.
- Lightweight M2M: The server side of LwM2M is delivered by Eclipse Wakaama (C/C++) and the client side by Eclipse Leshan (Java). Wakaama provides an API for server applications to send commands to registered LwM2M clients. Leshan relies on the Eclipse IoT Californium project for the CoAP and DTLS implementation.
- DNSSEC: Eclipse Tiaki provides a DNSSEC implementation in Java. Domain Name System Security Extensions (DNSSEC) is specified by IETF for securing certain kinds of information provided by the Domain Name System (DNS).
- DTLS: Eclipse TinyDTLS implements the Data Transport Layer Security (DTLS) standard in C. The implementation covers both the client and the server state machine. DTLS in general is a communication protocol that provides security also for datagram protocols like UDP.
Gateways
A gateway manages the connectivity between devices and provides a platform for the upper applications. Eclipse Kura offers a set of services that helps to manage the devices and applications deployed onto IoT gateways. Same to other Eclipse projects the gateway is based on Java and OSGi services. Kura manages the cloud connectivity, supports different protocols and configures the network.
Frameworks
Eclipse IoT provides a set of frameworks:
- Eclipse SmartHome is a set of Java and OSGi services for building and running Smart Homes. It is designed to run on “simple” devices like Raspberry Pi, BeagleBone Black or Intel Edison. Additionally, this framework supports typical protocols with their diversity used in Smart Homes like EnOcean, KNX or ZigBee. Most of all this way allows the devices and systems to communicate with each other. Almost the new version 0.8 of Eclipse Smart Home contains now a new REST interface that allows easier interaction with the clients. Furthermore, new bindings are supported, e.g. for DigitalStrom.
- Eclipse SCADA is a set of Java and OSGi services that implements nearly all of the services required to run a SCADA (supervisory control and data acquisition) system. As one type of an Industrial Control System (ICS) Eclipse SCADA delivers functions for data acquisition, monitoring, visualization, etc. Additionally, the framework supports typical industrial automation standards like ModBus, Siemens PLC, SNMP and OPC.
- Eclipse OM2M is one implementation of ETSI’s MSM standard. This implementation provides a horizontal Service Capability Layer (SCL) to be deployed in a M2M network.
Summary
In conclusion Eclipse IoT provides an open source stack including all relevant frameworks, protocols and standards to develop your own IoT application. The stack allows you to develop new devices but also to modernise existing ‘legacy’ devices.